CCTV and Surveillance Systems
BUILDEX specialists in CCTV security and surveillance solutions. Supply, installation and maintenance system monitored from central control point. Closed circuit TV (CCTV) is used in many different applica-tions. Some products are used in banks, casinos, or retail stores. Other are designed for military applications or to monitor traffic patterns on roadways. A CCTV security camera can also be used to monitor shoppers or pedestrians in open-air spaces. Many closed-circuit TV (CCTV) systems meet regulatory requirements or adhere to guidelines from the International Standards Organization (ISO).
CCTV, Closed Circuit Television, is today rapidly becoming a key component in modern security systems. Buildex offers fully integrated and flexible CCTV surveillance monitored from one central control point to en-sure safe and controlled environment to you and guests and to prevent unauthorized access to your premis-es.
With one person monitoring from central control point a series of events happening simultaneously, the sys-tem provides cost effective productivity as well as higher standard of safety. The system enables security to monitor every zone in the building.


Access Control Systems
Access control, security and biometrics equipment is used to monitor and restrict access to equipment, parts of buildings, or entire facilities. Building access controls include security devices such as entry key cards and fobs, entry key locks and pads, and biometric techniques such as fingerprint, face, and voice recognition.
Biometric access control systems use special scanners or devices, as well as building access control software that includes recognition algorithms and databases.
The time and attendance and access control markets continue to experience significant growth in the use of biometric devices. Used in conjunction with labor management soft-ware, biometric devices can make a considerable contribution to the reduction of labor costs in an organization. A company’s line management can eliminate card fraud and also monitor its staff’s attendance in real-time. Supervisors can run a report at any time to determine which employees arrived late or are absent and follow up accordingly.
The system is easy to use. Employees punch in their number and present their hand. The number retrieves the stored template and their identity is automatically verified. The reader shows an indicator light and emits a beep to indicate an ‘accept’ or ‘decline’ signal.
Beyond being a time and attendance clock, the biometric reader also has data management keys that allow for labor cost transfers when employees punch. Thus employees’ labor cost can be allocated to a new cost centre as they clock on duty.
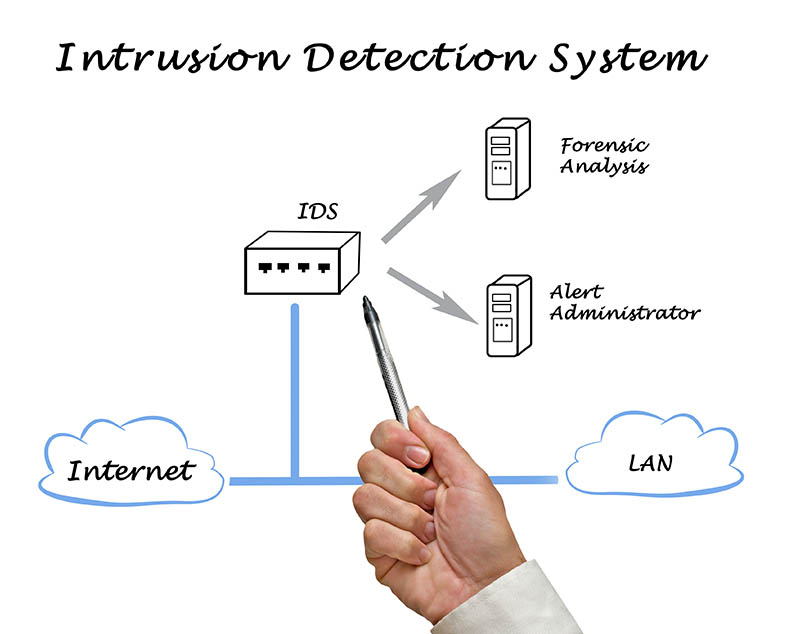
Intrusion Detection System
An intrusion detection system (IDS) monitors network traffic and monitors for suspicious activity and alerts the system or network administrator. In some cases the IDS may also respond to anomalous or malicious traffic by taking action such as blocking the user or source IP address from accessing the network.
IDS come in a variety of “flavors” and approach the goal of detecting suspicious traffic in different ways.
There are network based (NIDS) and host based (HIDS) intrusion detection systems. There are IDS that detect based on looking for specific signatures of known threats- similar to the way antivirus software typically detects and protects against malware- and there are IDS that detect based on comparing traffic patterns against a baseline and looking for anomalies. There are IDS that simply monitor and alert and there are IDS that perform an action or actions in response to a detected threat. We’ll cover each of these briefly.